SAML Configuration for On-Premises
This document describes how to configure Authentication and Authorization in an On-Premises environment using SAML (Security Assertion Markup Language). SAML enables enterprises to authenticate users to access OverOps by storing credentials on an external SAML server.
To enable SAML for OverOps you need to have access to the IP address and hostname of the SAML server. SAML configuration for OverOps is carried out from the On-Premises server properties file.
Authentication
Authentication is the process through which users are verified at login. By default, user accounts are managed by the OverOps analysis server. User accounts managed by OverOps, are stored and encrypted using Bcrypt (industry standard with salt strings).
OverOps also natively supports integrations with SAML to synchronize with the chosen identity management solution.
To configure SAML as the default authentication method for on-premises deployment, you need to prepare the IdP Metadata XML by setting the service provider.
To prepare the IdP Metadata XML:
-
From the SAML server, create a new service provider (SP), with the following parameters:
a. entityId:
http://<SERVER_HOSTNAME>:8080/saml/global
for example: http://overops.example.com:8080/saml/globalb. consumerUrl:
This should be the same as entityId.c. NameId format: EmailAddress
-
Generate an IdP Metadata XML that will be configured in the next step.
To enable SAML:
-
From
/opt/takipi-server/conf/tomcat/shareddirectory, open themy.server.propertiesfile. -
In the
my.server.propertiesfile, comment out and fill in the SAML parameters as follows:a. **GLOBAL_DOMAIN_AUTH_ENABLED**=true b. **GLOBAL_DOMAIN_AUTH_TYPE**=SAML c. **LDAP_SAML_GROUPS_FIELD_NAMES**=When using SAML to set the authorization level in the SAML assertion, you need to set the SAML attribute name you will use to pass the authorization info (Environments and Role pairs, see in here for more information). OverOps will search for this attribute name while validating the SAML assertion for the logged in user. The default attribute name if not otherwise set is: overops-groups
d. **SAML_BASIC_SSO_MODE_DEFAULT_ROLE**= <see supported options below>When using SAML in basic SSO mode (without using the Groups attribute), or when using the Backwards-Compatibility mode with an empty Groups attribute - OverOps will use a default authorization level for all authenticated users on all existing domain environments. As a security best practice (and in order to avoid users being denied or granted permissions in all environments) you should set this property with your desired default level of default permission. The available options are: No_Access / Viewer / Member.
Using No_Access means that any authenticated user which is not specifically given specific access (using the SAML Groups attribute) will be denied access to all environments for the domain.e. **GLOBAL_DOMAIN_AUTH_SAML_IDP_METADATA**=Remove all line breaking characters from the SAML IdP metadata XML content and paste it here.
Example:
GLOBAL_DOMAIN_AUTH_SAML_IDP_METADATA=<?xml version="1.0" encoding="UTF-8"?><md:EntityDescriptor xmlns:md="urn:oasis:names:tc:SAML:2.0:metadata" entityID="http://www.example.com"....
Note: Starting from release 4.45 we support a new property: GLOBAL_DOMAIN_AUTH_SAML_IDP_METADATA_FILE =<SAML metadata file.xml>.
This property can be used in order to point to an external SAML metadata.xml instead of specifying the metadata inside my.server.properties configuration file. The path for the metadata file can either be a relative file path (the file will be searched in the configuration directories) or an absolute path.
Optional properties:
The provided default includes the standard options for extracting the correct email, lastname, firstname and other parameters from the SAML server. All parameter names in the default string are matched against the SAML server and the relevant one is used:
f. LDAP_SAML_EMAIL_FIELD_NAMES=Set the property names for the email property. Default: “mail;email”
g. LDAP_SAML_FIRSTNAME_FIELD_NAMES=Sets the property names for the first name property. Default: “gn;givenName;firstName”
h. LDAP_SAML_LASTNAME_FIELD_NAMES
Sets the property names for the last name property. Default: “sn;surName;lastName”
i. LDAP_SAML_PHONE_FIELD_NAMES
Sets the property names for the phone property. Default: “telephoneNumber;phone;telephone;phoneNumber”
GLOBAL_DOMAIN_AUTH_ENABLED=true
GLOBAL_DOMAIN_AUTH_TYPE=SAML
GLOBAL_DOMAIN_AUTH_SAML_IDP_METADATA=<?xml version="1.0" encoding="UTF-8"?><md:EntityDescriptor xmlns:md="urn:oasis:names:tc:SAML:2.0:metadata" entityID="http://www.example.com"....
LDAP_SAML_EMAIL_FIELD_NAMES=email;mail
LDAP_SAML_FIRSTNAME_FIELD_NAMES=gn;givenName;firstName
LDAP_SAML_LASTNAME_FIELD_NAMES=sn;surName;lastName
LDAP_SAML_PHONE_FIELD_NAMES=telephoneNumber;phone;telephone;phoneNumberAuthorization
Authorization is the control mechanism that allows authenticated users to view or change certain information.
Owners of each environment key (identified by a unique environment key) have Admin capabilities.
Admins are authorized to change key and security settings, while retaining the ability to access information. They can edit code redaction policies, Storage Server location, manage user roles, etc. Admin users can set other users’ roles, and set the IP address range, from which authenticated users can access the key, to a specific network or VPN.
Members access is limited. Members may view snapshots, create views, and access information in OverOps, but they cannot change key or security configurations.
Viewers gain read-only access to the environment.
A viewer can access the Events explorer, edit event notes, access the different team views, the ARC screens and the Reliability Dashboard.
However a Viewer will have limited access to the Settings, to the API and will not be allowed to invite other members to the Key or to generate a new environment keys (a viewer will be allowed to create new keys only if this user has different roles in other environments).
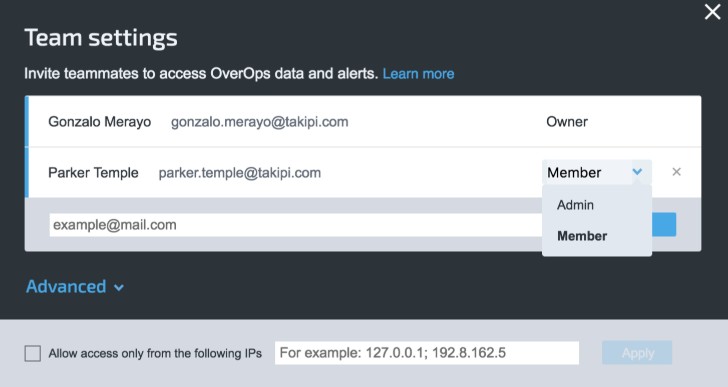
Manage access of team members and IP access points
Automatic Distribution of Environment Keys
Every active environment key generated by the global domain initializer can be automatically shared with users logged in via SAML.
To configure automatic key distribution:
In the my.server.properties file, comment out and fill in the global domain initializer:
GLOBAL_DOMAIN_INITIALIZER=
Updated 10 months ago
